Honestly, I really don't know why i felt like pulling up a new post window.
Just a few moments ago I walked into my apartment coming home from work and threw myself on my makeshift bed.
This blog is going back to being extremely introspective.
It is now a placeholder for rhetorical questions even the sanest human beings I know can't answer.
I am back to living on my own. There is and odd pleasure about having your own living room, your own kitchen, your own balcony, and your own room where no one can peek in unless you let them.
I noticed there was no trouble getting adjusted to the loneliness that comes with it.
It is better this way I think.
************************************************************
Actually, the reason I did this was to let out that I miss Ellen.
************************************************************
There will probably be a more lengthy post later.
Tuesday, August 9, 2011
Thursday, May 26, 2011
HOW TO: Crack WEP Security
Today i have a very special post for everyone who follows this blog.
The method i am about to show you will become somewhat useless in the future. I will show you WHY. Everyday more and more people are switching over to WPA and WPA2 for wireless security. More and more router manufacturers are setting WPA as the default security standard of their routers. I would love to go into the history of wireless security, but i want to keep this post short and to the point. all you have to know is that WPA is definitely MORE SECURE than WEP.
As this is a public blog, i shall emphasize that i am posting this for educational purposes only.
You have to understand that i try to be as ethical as possible with the knowledge i've acquired over the years.
"What is ethical about showing people this information?" you might ask.
I gathered my knowledge from multiple free and open sources on the internet. Information should be free and open to anyone. YOU have the same right to it as I do and YOU make the choice on what to do with it.
This is my own personal belief, plain and simple.
The laws regarding unauthorized access to wifi networks varies from state to state
I am posting the following link as a WARNING to those who may have abusive/ill intent:
http://www.ncsl.org/IssuesResearch/TelecommunicationsInformationTechnology/ComputerHackingandUnauthorizedAccessLaws/tabid/13494/Default.aspx
it's not my place to choose between right and wrong for you
Moving on...
(If some descriptions seem Vague to you, i purposely mean to have it that way. If you really care, you'll do some research on your own)
WHAT YOU WILL NEED:
- A DESKTOP COMPUTER OR LAPTOP
herp derp on this right? I know you are not idiots, but we only know about idiots cause they exist, and we have all met at least one.......lets leave it a that.
- A PROPER WIRELESS ADAPTER
In this particular procedure I will be working with a NETGEAR WG111v2 wireless adapter. This is probably the trickiest part, believe it or not, mainly because you have to find it and probably spend some money on it. There are many wireless adapters out there from many manufacturers. What makes this Netgear adapter so special Manni? The firmware inside of it.
Again to keep this short, you can find lists of adapters which have a firmware suitable for WEP and WPA cracking online.
- BACKTRACK 3 (LINUX)
YES, you read Linux.........does this intimidate you? don't let it. Backtrack is an operating system which can be run from a Linux "Live-CD." This means you can load the CD into your CD-ROM drive and restart your computer. The Live-CD loads automatically with Linux on your computer. most of yours will say something like "press any key to boot from CD" or something similar. The neat thing about live CD's is that you can take out the Live-CD and restart your computer and Windows/OSx (yup they are Mac friendly) will load up as if nothing ever happened. They are completely safe to use.
For the purposes of my own procedure I run a program called VMware which lets me simulate a virtual computer on my desktop. Naturally i loaded the BACKTRACK3.ISO file.
THE HACK:
I have read multiple guides out there on how to do this and most ALL use a program called Aircrack-ng. They involve inputting command lines to achieve the feat I am going to perform, BUT to make it easy on YOU, it will be based on programs that have a Graphical User Interface. What does this mean Manni? it means pretty pictures! NO COMMAND LINES!
-Step one
Make sure Backtrack 3 detected the Wireless adapter. The easiest way to check for this is to open the "Wireless Assistant" from the Backtrack 3 Start menu.
When the program opens it will say "Initializing" at the bottom. If you have a proper wireless adapter it will begin displaying wireless networks for you to connect to. If you see wireless connections on the list it means the adapter is working. go ahead and close the program.
-Step Two
We are now ready to Sniff out wireless networks. How is this different than just using the Wireless Assistant to find wireless networks? A Sniffer will not only go out and find wireless networks, It will give you other variables specific to the wireless network such as the MAC Address, BSSID, Channel, and Packet Count...etc.
The Sniffer program we will use is called KISMET. I'll be honest KISMET is not technically a Sniffer but i use this term because i relate it to looking for specific information which may be useful. There are programs that have better functionality than KISMET, but it's what i feel comfortable using.
to open KISMET in BACKTRACK 3:
You will get the following window:
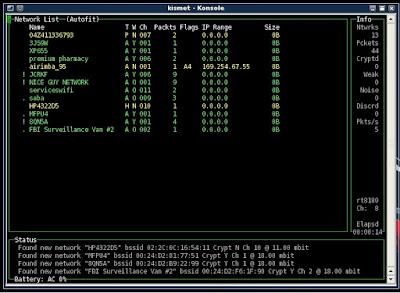
What we want at this point is to sort the networks by "PACKET COUNT"
you can achieve this by pressing the letter "S" to open the sort menu, Then press "P" to sort by packet count. You want to find a WEP secured network with the highest packet count. You have to understand that Signal strength DOES NOT always mean high packet count.
In Kismet the networks with the highest packet count will go to the bottom of the list and that is where we want to start after sorting:
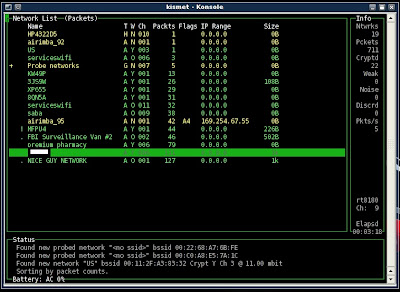
Scroll down with the arrows on your keyboard and hit enter on a network. DISREGARD THE NETWORK NAME for the moment. The goal is to find a network that is WEP secured. We select and press "enter" on a network and press "Q" to return back to the list of networks
so what are we looking for manni?
what you need from this window are 3 things
"Encrypt : WEP"--tells us this is in fact a WEP secured network
"BSSID : 00:24:D2:B9:25:22" -- Tells us the BSSID which is the network's MAC address
"Channel : 6" -- tells us the CHANNEL number of the network. this number will always be between 1 and 11
***WRITE THIS INFORMATION DOWN. YOU WILL NEED IT***
This is what it looks like:
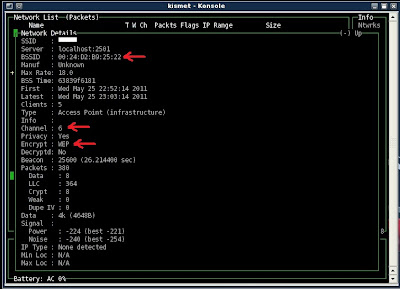
you may now close Kismet and proceed...
-Step Three
At this point we have found the network we want to access, you may have noticed I whited-out the actual name of the network for my own protection. though you can still see the BSSID and the CHANNEL number.
really that's all you need when cracking WEP security.
we will now open a program called SpoonWep.
Start >> Backtrack >> Radio Network Analysis >> 80211 >> Cracking >> SPoonWep
You will notice immediately why i love this program.
All we have to do now is input the information we gathered from kismet.
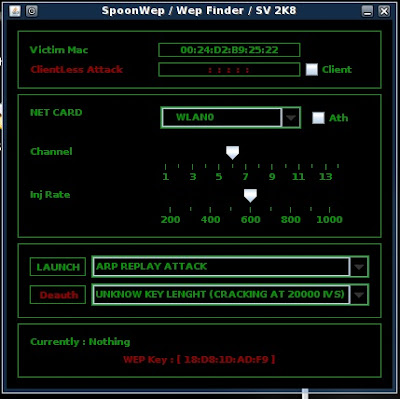
In "Victim Mac" we simply input the BSSID
In the "NET CARD" drop-down you select your wireless adapter. In most cases it is called "Wlan0"
Then, we slide the channel selector to the proper channel gathered from Kismet
***DISREGARD ALL OTHER VARIABLES***
Yeah, i could definitely explain what they mean but for the purposes of learning a simple hack they will be irrelevant to you. Though, I will point out the name of the hack. It is called an "ARP REPLAY ATTACK"
It will look like this:
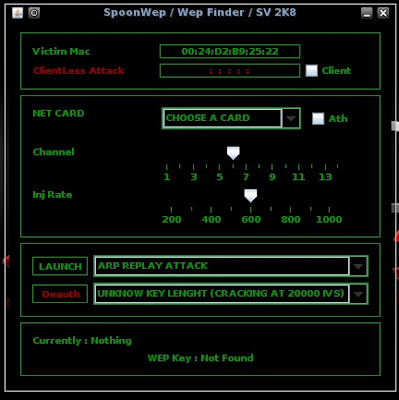
We want to subsequently "LAUNCH" the attack.
A window called "WS DUMP" will appear
It will have a variable called "#Data" that increases in number when you are running the attack.
These are called IV's and they are the information used to defeat the WEP algorithm. Depending on how far away the network is this process will vary in time. Most new computers can do it in around 1 - 5 minutes. Sometimes the #data count will go very slow and it may take up to 10 - 15, even 20 minutes. BE PATIENT.
you notice on the background we also have SpoonWep counting IV's and giving you a status of "CRACKING WEP"
Here's what that looks like:
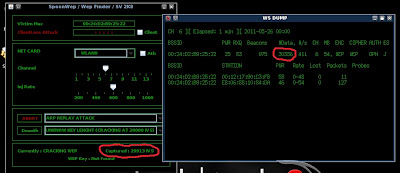
SpoonWep begins cracking the WEP key once is reaches the 20,000 mark, but the more IV's you gather the faster it will finish the attack. Again let me reiterate, if the IV count is going slow just BE PATIENT. As long as it is going up to 20,000 and above, the program WILL eventually decrypt the WEP key for you.
If all goes as I've explained then you will get:
As you can see SpoonWep is displaying the WEP key for the network we found in Kismet
SpoonWep displays it separated by colons, but just disregard those. All 40-bit wep keys are exactly 10 characters long and 128-bit keys are 26 charaters long.
we just cracked a 40-bit WEP key.
And now we are DONE! YAAAY!!!
We never once opened the command line interface during this hack
not only that, It was extremely EASY.
And THIS my friends is WHY we see the standard changing from WEP to WPA/WPA2.
I hope i was able to teach you something interesting.
Have a great rest of your day/night.
The method i am about to show you will become somewhat useless in the future. I will show you WHY. Everyday more and more people are switching over to WPA and WPA2 for wireless security. More and more router manufacturers are setting WPA as the default security standard of their routers. I would love to go into the history of wireless security, but i want to keep this post short and to the point. all you have to know is that WPA is definitely MORE SECURE than WEP.
As this is a public blog, i shall emphasize that i am posting this for educational purposes only.
You have to understand that i try to be as ethical as possible with the knowledge i've acquired over the years.
"What is ethical about showing people this information?" you might ask.
I gathered my knowledge from multiple free and open sources on the internet. Information should be free and open to anyone. YOU have the same right to it as I do and YOU make the choice on what to do with it.
This is my own personal belief, plain and simple.
The laws regarding unauthorized access to wifi networks varies from state to state
I am posting the following link as a WARNING to those who may have abusive/ill intent:
http://www.ncsl.org/IssuesResearch/TelecommunicationsInformationTechnology/ComputerHackingandUnauthorizedAccessLaws/tabid/13494/Default.aspx
it's not my place to choose between right and wrong for you
Moving on...
(If some descriptions seem Vague to you, i purposely mean to have it that way. If you really care, you'll do some research on your own)
WHAT YOU WILL NEED:
- A DESKTOP COMPUTER OR LAPTOP
herp derp on this right? I know you are not idiots, but we only know about idiots cause they exist, and we have all met at least one.......lets leave it a that.
- A PROPER WIRELESS ADAPTER
In this particular procedure I will be working with a NETGEAR WG111v2 wireless adapter. This is probably the trickiest part, believe it or not, mainly because you have to find it and probably spend some money on it. There are many wireless adapters out there from many manufacturers. What makes this Netgear adapter so special Manni? The firmware inside of it.
Again to keep this short, you can find lists of adapters which have a firmware suitable for WEP and WPA cracking online.
- BACKTRACK 3 (LINUX)
YES, you read Linux.........does this intimidate you? don't let it. Backtrack is an operating system which can be run from a Linux "Live-CD." This means you can load the CD into your CD-ROM drive and restart your computer. The Live-CD loads automatically with Linux on your computer. most of yours will say something like "press any key to boot from CD" or something similar. The neat thing about live CD's is that you can take out the Live-CD and restart your computer and Windows/OSx (yup they are Mac friendly) will load up as if nothing ever happened. They are completely safe to use.
For the purposes of my own procedure I run a program called VMware which lets me simulate a virtual computer on my desktop. Naturally i loaded the BACKTRACK3.ISO file.
THE HACK:
I have read multiple guides out there on how to do this and most ALL use a program called Aircrack-ng. They involve inputting command lines to achieve the feat I am going to perform, BUT to make it easy on YOU, it will be based on programs that have a Graphical User Interface. What does this mean Manni? it means pretty pictures! NO COMMAND LINES!
-Step one
Make sure Backtrack 3 detected the Wireless adapter. The easiest way to check for this is to open the "Wireless Assistant" from the Backtrack 3 Start menu.
start >> Internet >> Wireless Assistant
When the program opens it will say "Initializing" at the bottom. If you have a proper wireless adapter it will begin displaying wireless networks for you to connect to. If you see wireless connections on the list it means the adapter is working. go ahead and close the program.
-Step Two
We are now ready to Sniff out wireless networks. How is this different than just using the Wireless Assistant to find wireless networks? A Sniffer will not only go out and find wireless networks, It will give you other variables specific to the wireless network such as the MAC Address, BSSID, Channel, and Packet Count...etc.
The Sniffer program we will use is called KISMET. I'll be honest KISMET is not technically a Sniffer but i use this term because i relate it to looking for specific information which may be useful. There are programs that have better functionality than KISMET, but it's what i feel comfortable using.
to open KISMET in BACKTRACK 3:
Start >> Backtrack >> Radio Network Analysis >> 80211 >> Analyser >> Kismet
You will get the following window:

What we want at this point is to sort the networks by "PACKET COUNT"
you can achieve this by pressing the letter "S" to open the sort menu, Then press "P" to sort by packet count. You want to find a WEP secured network with the highest packet count. You have to understand that Signal strength DOES NOT always mean high packet count.
In Kismet the networks with the highest packet count will go to the bottom of the list and that is where we want to start after sorting:

Scroll down with the arrows on your keyboard and hit enter on a network. DISREGARD THE NETWORK NAME for the moment. The goal is to find a network that is WEP secured. We select and press "enter" on a network and press "Q" to return back to the list of networks
so what are we looking for manni?
what you need from this window are 3 things
"Encrypt : WEP"--tells us this is in fact a WEP secured network
"BSSID : 00:24:D2:B9:25:22" -- Tells us the BSSID which is the network's MAC address
"Channel : 6" -- tells us the CHANNEL number of the network. this number will always be between 1 and 11
***WRITE THIS INFORMATION DOWN. YOU WILL NEED IT***
This is what it looks like:

you may now close Kismet and proceed...
-Step Three
At this point we have found the network we want to access, you may have noticed I whited-out the actual name of the network for my own protection. though you can still see the BSSID and the CHANNEL number.
really that's all you need when cracking WEP security.
we will now open a program called SpoonWep.
Start >> Backtrack >> Radio Network Analysis >> 80211 >> Cracking >> SPoonWep
You will notice immediately why i love this program.
All we have to do now is input the information we gathered from kismet.
In "Victim Mac" we simply input the BSSID
In the "NET CARD" drop-down you select your wireless adapter. In most cases it is called "Wlan0"
Then, we slide the channel selector to the proper channel gathered from Kismet
***DISREGARD ALL OTHER VARIABLES***
Yeah, i could definitely explain what they mean but for the purposes of learning a simple hack they will be irrelevant to you. Though, I will point out the name of the hack. It is called an "ARP REPLAY ATTACK"
It will look like this:

We want to subsequently "LAUNCH" the attack.
A window called "WS DUMP" will appear
It will have a variable called "#Data" that increases in number when you are running the attack.
These are called IV's and they are the information used to defeat the WEP algorithm. Depending on how far away the network is this process will vary in time. Most new computers can do it in around 1 - 5 minutes. Sometimes the #data count will go very slow and it may take up to 10 - 15, even 20 minutes. BE PATIENT.
you notice on the background we also have SpoonWep counting IV's and giving you a status of "CRACKING WEP"
Here's what that looks like:

SpoonWep begins cracking the WEP key once is reaches the 20,000 mark, but the more IV's you gather the faster it will finish the attack. Again let me reiterate, if the IV count is going slow just BE PATIENT. As long as it is going up to 20,000 and above, the program WILL eventually decrypt the WEP key for you.
If all goes as I've explained then you will get:

As you can see SpoonWep is displaying the WEP key for the network we found in Kismet
SpoonWep displays it separated by colons, but just disregard those. All 40-bit wep keys are exactly 10 characters long and 128-bit keys are 26 charaters long.
we just cracked a 40-bit WEP key.
And now we are DONE! YAAAY!!!
We never once opened the command line interface during this hack
not only that, It was extremely EASY.
And THIS my friends is WHY we see the standard changing from WEP to WPA/WPA2.
I hope i was able to teach you something interesting.
Have a great rest of your day/night.
Saturday, May 21, 2011
CRAIGSLIST PAYPAL SCAM
I suppose this will be a sort of public service announcement. It is hard to determine how rampant this SCAM is and how many victims it has claimed.
To give you a bit of a background:
I am a somewhat well rounded computer tech/IT guy. I know plenty to be more than just dangerous (i'll leave it at that). From time to time i end up with extra computer hardware in my dealings. You know, extra monitors, extra computers, extra cpu's, extra ram, hard drives, miscellaneous electronics, etc. Most savvy computer techs will generally be in the same situation and will have a box or closet in the house/apartment dedicated to this. Naturally we eventually run out of space and decide to sell off some of our stuff. this is where Craigslist comes in.
Recently i posted several computer systems for sale and a lot or miscellaneous computer related electronics
here they are in case anyone is interested,
http://dallas.craigslist.org/ndf/sys/2368274445.html
http://dallas.craigslist.org/ndf/sys/2368241837.html
http://dallas.en.craigslist.org/ndf/sys/2368262809.html
anyway...
so after feeling a bit accomplished to know i'm on my way to getting rid of all of this stuff, my email inbox did not sit still for long
almost immediately i got a replay from a so called "Jojo Brad" at email address "radjojo8@gmail.com"
and it stated the following:
mind boggling, yes indeed......But then, something else happened.
I get yet another response from a supposedly different person with something which looked like the same message, just modified a little.
Of course, thankfully, i did not fall for it.
It did however crush some hopes that i would get rid of some stuff and have extra cash in my pocket.
From what i read online in random forums is that they try to get you to give them your paypal email address. I found no evidence that they actually tamper with your account in any way, but again i really honestly don't know. Once they have your Email address they send back a fake official looking email that seems to come from Paypal, but it really doesn't. I believe they make an argument to say that they have fulfilled their end of the bargain because their fake accounts shows they have paid you, but your real Paypal account shows no record of transaction.
If you happened to send the item, Paypal has no fault and no record of a transaction.
The scanmer just walked away with your goods for free....
PLEASE all of you stay safe out there if you use Paypal
make sure the transaction goes through on the Paypal website and that the user's account has been verified. This particular scam is not the most intricate, but if they keep doing it, it means they have succeeded in the past and are willing to try and repeat the feat.
DON'T LET IT BE YOU!
thanks for reading followers
on a side note:
I might consider starting a FOLLOWER OF THE WEEK! post every week.
I browse through blogspot quite a bit and sometimes there are posts that stand out more than others and stay with you long after you are done reading them.
As a featured follower i will recommend that everyone who reads the post follow the person in hope that they too might find something interesting to ready
good idea? bad idea?
To give you a bit of a background:
I am a somewhat well rounded computer tech/IT guy. I know plenty to be more than just dangerous (i'll leave it at that). From time to time i end up with extra computer hardware in my dealings. You know, extra monitors, extra computers, extra cpu's, extra ram, hard drives, miscellaneous electronics, etc. Most savvy computer techs will generally be in the same situation and will have a box or closet in the house/apartment dedicated to this. Naturally we eventually run out of space and decide to sell off some of our stuff. this is where Craigslist comes in.
Recently i posted several computer systems for sale and a lot or miscellaneous computer related electronics
here they are in case anyone is interested,
http://dallas.craigslist.org/ndf/sys/2368274445.html
http://dallas.craigslist.org/ndf/sys/2368241837.html
http://dallas.en.craigslist.org/ndf/sys/2368262809.html
anyway...
so after feeling a bit accomplished to know i'm on my way to getting rid of all of this stuff, my email inbox did not sit still for long
almost immediately i got a replay from a so called "Jojo Brad" at email address "radjojo8@gmail.com"
and it stated the following:
"Thanks for getting back to me as soon as you can i am buying this forIt was immediately fishy who pays more than they have to???
my cousin,And i wont be able to pick it up due to my working hours i
would like it shipped to my cousin i would offer you $500 including
shipping and stress i would be paying you through paypal to make this
faster get back to me with your paypal email address asap so we can do
this i need it shipped today get back to me asap.Thanks.
I await your quick response."
mind boggling, yes indeed......But then, something else happened.
I get yet another response from a supposedly different person with something which looked like the same message, just modified a little.
"Thanks for getting back to me as soon as you can i am buying this forThat's when i knew it was all a SCAM!
my cousin,And i wont be able to pick it up due to my working hours i
would like it shipped to my cousin i would offer you $420 including
shipping and stress i would be paying you through paypal to make this
faster get back to me with your paypal email address asap so we can do
this i need it shipped today get back to me asap.Thanks.
I await your quick response."
Of course, thankfully, i did not fall for it.
It did however crush some hopes that i would get rid of some stuff and have extra cash in my pocket.
From what i read online in random forums is that they try to get you to give them your paypal email address. I found no evidence that they actually tamper with your account in any way, but again i really honestly don't know. Once they have your Email address they send back a fake official looking email that seems to come from Paypal, but it really doesn't. I believe they make an argument to say that they have fulfilled their end of the bargain because their fake accounts shows they have paid you, but your real Paypal account shows no record of transaction.
If you happened to send the item, Paypal has no fault and no record of a transaction.
The scanmer just walked away with your goods for free....
make sure the transaction goes through on the Paypal website and that the user's account has been verified. This particular scam is not the most intricate, but if they keep doing it, it means they have succeeded in the past and are willing to try and repeat the feat.
DON'T LET IT BE YOU!
thanks for reading followers
on a side note:
I might consider starting a FOLLOWER OF THE WEEK! post every week.
I browse through blogspot quite a bit and sometimes there are posts that stand out more than others and stay with you long after you are done reading them.
As a featured follower i will recommend that everyone who reads the post follow the person in hope that they too might find something interesting to ready
good idea? bad idea?
Friday, May 20, 2011
uneasy
So i came home from work today and didn't have much to do.
I decided to browse Netflix until i came upon the documentary "Countdown to Zero"
It's about the very real threat of a nuclear bomb detonating due to circumstances other than defense, such as a microchip malfunction, or am improper execution of protocols.
As the title suggests, I began to feel uneasy
A quote told to me by a dear friend came to mind
I shall not name him but it went something like this
"I refuse to be part of something in which the goal is to figure out how to kill more people faster"
It may not be exact but it's how i remember it
A renewed fervor has awakened in me to make free energy work
I believe I have found my life long calling
all of that aside...
i've yet to figure out a specific theme for this blog
i guess it'll just be about ME! yes that is it.
posts will be arranged in a somewhat erratic manner and even when i'm done for that particular day i might come back and edit.
actually, that's what happened to this one......
i will put bold titles for random specific blocks of thought coming out as i type.
I decided to browse Netflix until i came upon the documentary "Countdown to Zero"
It's about the very real threat of a nuclear bomb detonating due to circumstances other than defense, such as a microchip malfunction, or am improper execution of protocols.
As the title suggests, I began to feel uneasy
A quote told to me by a dear friend came to mind
I shall not name him but it went something like this
"I refuse to be part of something in which the goal is to figure out how to kill more people faster"
It may not be exact but it's how i remember it
A renewed fervor has awakened in me to make free energy work
I believe I have found my life long calling
all of that aside...
i've yet to figure out a specific theme for this blog
i guess it'll just be about ME! yes that is it.
posts will be arranged in a somewhat erratic manner and even when i'm done for that particular day i might come back and edit.
actually, that's what happened to this one......
i will put bold titles for random specific blocks of thought coming out as i type.
Thursday, May 19, 2011
i may continue
well it's been a while since my previous post
i'll try go gather myself very soon to give a more detailed description of my recent self
i'll try go gather myself very soon to give a more detailed description of my recent self
Monday, April 5, 2010
oh life....
you're throwing too much at once in my direction
it's going to be an interesting 4 months
it's going to be an interesting 4 months
Saturday, March 27, 2010
can't sleep
so i turned 24
it does not feel much different
on Sunday i get to pick up Ellen and we're going to spend the day together
it's going to be nice
recently i've been reading up too many things
my brain is a bit overloaded with information
on antisemitism,
some of the definitions on the term are very extreme and some are just loose. violent acts of hate against a specific group is not something i would ever consider. although, what if this group of people is doing just that against others? in that case i don't really care what kind of culture you have. the right to lead a free life belongs to everyone. Being against the state of israel for denying basic human rights to Palestinians apparently is antisemitic.
how does this happen
everything has to be this sort of reverse racism mantra when it comes to jews
to me they seem to bring the prejudice upon themselves and they do it very well
origins of the aryan race
well it had nothing to do with the planet earth, i'll tell you that much
the concept of a master race doesn't really apply to human beings
how it came to be adopted might have come from an over exaggeration of fictional literature
there may be some facts about the origins
but i do not agree in the "master" part
they're just another race
free energy
the general consensus is that somehow free energy devices are transforming energy from the environment into usable work, mainly a movement of electrons. they key of it all lies in creating the conditions for an adequate medium for this new type of energy. i do not think we will come up with anything for a while. i could be wrong, but our thinking was not ever nurtured into thinking about maybe having in infinite amount of energy. the concept of scarcity is much too rooted in the mind of those who do this kind of research. we need a new breed of researchers to become free from old ways of thinking.
working out
well i'm finally doing the classic version of p90x. i had to skip today's workout. i was way too tired. hopefully i can fix my diet before i get too far into the program. that or i will just be a very pudgy very muscular guy.
personal finance
well i've started pumping as much money as i can into my savings
found out my bank has a great trading account deal
100 free trades! holy crap! this is going to be all kinds of great
i've have began to think of the stock market inversely
bear market means cheap buys
i will not be suckered into buying a stock on it's way up
of course that sounds like an oxymoron
but there's a good explanation to it when you know what you're doing
let's hope i read enough before i blow all of my money
reading a book called tragedy and hope
western civilization. i wonder what will happen with us.
it does not feel much different
on Sunday i get to pick up Ellen and we're going to spend the day together
it's going to be nice
recently i've been reading up too many things
my brain is a bit overloaded with information
on antisemitism,
some of the definitions on the term are very extreme and some are just loose. violent acts of hate against a specific group is not something i would ever consider. although, what if this group of people is doing just that against others? in that case i don't really care what kind of culture you have. the right to lead a free life belongs to everyone. Being against the state of israel for denying basic human rights to Palestinians apparently is antisemitic.
how does this happen
everything has to be this sort of reverse racism mantra when it comes to jews
to me they seem to bring the prejudice upon themselves and they do it very well
origins of the aryan race
well it had nothing to do with the planet earth, i'll tell you that much
the concept of a master race doesn't really apply to human beings
how it came to be adopted might have come from an over exaggeration of fictional literature
there may be some facts about the origins
but i do not agree in the "master" part
they're just another race
free energy
the general consensus is that somehow free energy devices are transforming energy from the environment into usable work, mainly a movement of electrons. they key of it all lies in creating the conditions for an adequate medium for this new type of energy. i do not think we will come up with anything for a while. i could be wrong, but our thinking was not ever nurtured into thinking about maybe having in infinite amount of energy. the concept of scarcity is much too rooted in the mind of those who do this kind of research. we need a new breed of researchers to become free from old ways of thinking.
working out
well i'm finally doing the classic version of p90x. i had to skip today's workout. i was way too tired. hopefully i can fix my diet before i get too far into the program. that or i will just be a very pudgy very muscular guy.
personal finance
well i've started pumping as much money as i can into my savings
found out my bank has a great trading account deal
100 free trades! holy crap! this is going to be all kinds of great
i've have began to think of the stock market inversely
bear market means cheap buys
i will not be suckered into buying a stock on it's way up
of course that sounds like an oxymoron
but there's a good explanation to it when you know what you're doing
let's hope i read enough before i blow all of my money
reading a book called tragedy and hope
western civilization. i wonder what will happen with us.
Subscribe to:
Posts (Atom)